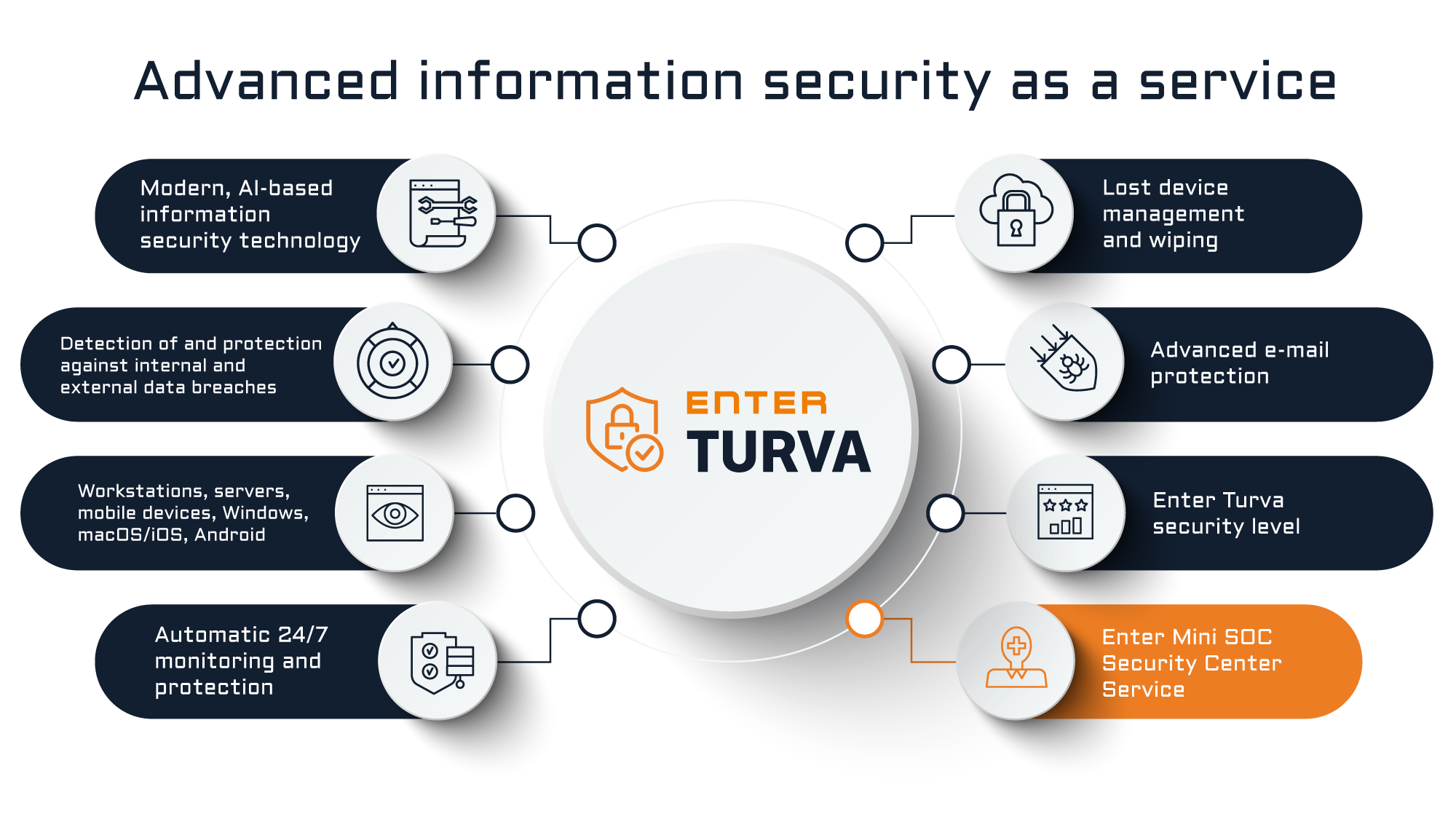
Enter Turva enables enterprise-level protection of endpoints and the use of other modern AI-based information security solutions in smaller organisations as well. The service is suitable for environments using workstations, servers or mobile devices.
Enter Turva combines virus protection, firewall and other traditional information security services with Microsoft’s artificial intelligence technology that monitors the status of your entire organisation’s IT environment. The service protects against zero-day threats, ransomware and other advanced malicious payloads. At the same time, it enables the deletion of data from stolen or lost devices and the setting of restrictions on copying, storing and sharing data.
Using Microsoft’s artificial intelligence technology, the service identifies deviating events in your organisation’s IT environment, helping protect against data breaches and malicious e-mail attachments.
Enter’s specialists constantly optimise the Enter Turva protection level, offering up-to-date information security definitions and settings with customer-specific adaptations.
Critical systems can be connected to Enter Valvomo. It includes reacting to alarms sent by the Enter Turva service in a specified manner, such as automatic corrective action.
Enter Turva
- Enterprise-level endpoint protection.
- Windows, macOS, iOS and Android.
- Automated protection against advanced viruses and malware.
- Detection of abnormal activity.
- Software inventories and vulnerability reports.
- Automatic alerts, corrective measures and protections for deviations detected in the IT environment.
- A replacement solution for traditional antivirus and firewall software.
- Restrictions on copying, storing and forwarding data.
- Remote wipe and lock of a stolen or lost device.
- Blocking of cloud services prohibited by the organisation.
- Rule-based protection and restrictions by time, place or device.
- Visual and real-time view of the status of the organisation’s information security.